How to detect if your devices are trying to circumvent your pihole
As I described in my previous blog post, you can set up a pi.hole DNS server to optimize your network traffic and your browsing experience. But not every device will be respecting your DHCP DNS settings it seems. Some devices have hardcoded DNS entries and just ignore your settings. Scott Helme wrote on his blog how to redirect those naughty devices and redirect their traffic to your pihole instead.
But before we start doing that I was curious to find how many of those devices I actually had on my network. To figure this out I had to setup my USG firewall to catch the TCP/UDP request on port 53 which are not originating from my pi-hole (on IP address 192.168.1.10). The USG firewall can be configured to log certain events on your firewall (without blocking the actions). This will show up in the log file on your USG. The log file can be found in /var/log/messages. You can view this file with the command:
tail -f /var/log/messages
Depending on your firewall configuration you will see almost nothing or a ton of information coming by. The goal is to capture these kind of events:
Oct 21 17:53:42 USG kernel: [WAN_OUT-2000-A]IN=eth1 OUT=eth0 MAC=80:2a:a8:f0:0a:49:94:9a:a9:23:23:40:08:00 SRC=192.168.1.186 DST=8.8.8.8 LEN=58 TOS=0x00 PREC=0x00 TTL=127 ID=59302 PROTO=UDP SPT=58633 DPT=53 LEN=38
What you see here is a request from IP address 192.168.1.186 doing a DNS request (DPT=53 meaning destination port 53 which is the port a DNS server listens to) to the DNS server at IP address 8.8.8.8.
A legitimate event would look like this:
Oct 21 17:55:05 USG kernel: [WAN_OUT-2000-A]IN=eth1 OUT=eth0 MAC=80:2a:a8:f0:0a:49:b4:fb:e4:8c:32:67:08:00 SRC=192.168.1.10 DST=1.1.1.1 LEN=57 TOS=0x00 PREC=0x00 TTL=63 ID=20414 DF PROTO=UDP SPT=23724 DPT=53 LEN=37
This is a DNS request coming from my pihole server on 192.168.1.10 and it’s configured to forward DNS requests to 1.1.1.1
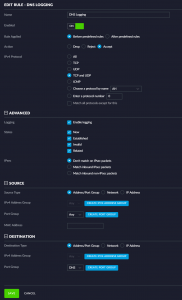
Let’s set up the firewall to start generating these logs in your log file. I have done this with Unifi version 5.9.29 Go to your cloud key settings page. Click Routing & Firewall. Click on firewall on the top of your screen. Click WAN OUT and click on Create New Rule. This is how my screen looks like:
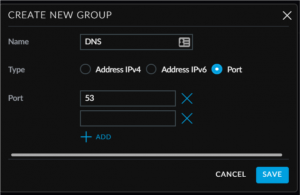
At the buttom you have to create a new Port group for the Destination. Click on create port group button and create one for DNS like I did below:
Make sure you click on the Add button after you filled in the port number (DNS listens to Port 53) before you hit save. Click Save again, This will cause your USG to be provisioned. SSH into your USG.
To only see all DNS request in your USG log file you can use the following command:
tail -f messages |grep -F “DPT=53 “
This will show any DNS requests going out to the internet, including the ones from your pihole. To only see the naughty devices you can use the following command (another grep, perhaps there is a more efficient way but this worked for me :)) where the IP address is the IP address of your pi-hole:
tail -f messages |grep -F “DPT=53 “| grep -v “SRC=192.168.1.10”
This one takes a while before it starts showing the log, but it worked for me. Now you will only see the DNS requests coming through your USG from your naughty devices. So how do you test this? The following command performs a DNS request and you can add a DNS server where the request is sent. This is a great way to test your setup:
nslookup techmeme.com 8.8.4.4
So far I have only seen a Samsung Galaxy S7 going to a Google DNS server directly. So the devices on my network seem to be well behaved.