Create a user delegated permission and an application permission with the same name in Azure Active Directory
For a training we are delivering I tried to create a little sample where I show how to create an API and protect it with our Microsoft Identity Platform. We have 2 kind of permissions we can support with our consent and permissions framework. User delegated permissions and application permissions. This is what we use for MS Graph as well.
User delegated permissions are used if you want to grant the app running the permissions in name of the user. For example I want the app to be able to read the users email. In our portal that’s very easy to setup in the application blade and select expose API.
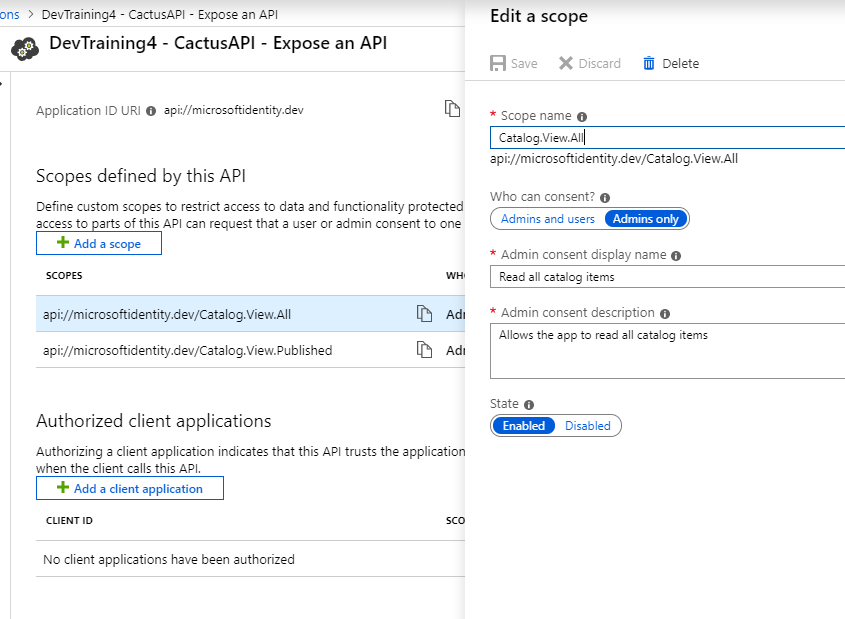
The second type of permissions are called application permissions. These permissions are used for daemon apps for example. Applications which don’t have user interaction directly. At this moment you cannot create these through the UI so you have to modify the manifest.
What I didn’t know until this week is how to create an app permission with the same name as the user delegated permission. For example the Catalog.View.All permissions is something I want to expose so a daemon app could call that API as well. Application permissions are created by creating roles in the manifest. It’s almost the same as user roles but with the little change that the allowedMemberTypes is Application instead of User.
"appRoles": [
{
"allowedMemberTypes": [
"Application"
],
"description": "Allows the app to read all catalog items",
"displayName": "Read all catalog items",
"id": "c399c4a5-75bd-4d13-95f4-6a66f84def67",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "Catalog.View.All"
}
],The one trick you have to do if you need the app permission to be the same as the user delegated permission is the id, displayname and description have to be exactly the same. So if you look in the manifest at the user delegated permission:
"oauth2Permissions": [
{
"adminConsentDescription": "Allows the app to read all catalog items",
"adminConsentDisplayName": "Read all catalog items",
"id": "c399c4a5-75bd-4d13-95f4-6a66f84def67",
"isEnabled": true,
"lang": null,
"origin": "Application",
"type": "Admin",
"userConsentDescription": "USER CONTENT, SHOULD NOT BE SHOWN WHEN ADMIN CONSENT ONLY",
"userConsentDisplayName": null,
"value": "Catalog.View.All"
}
],The adminConsentDisplay name needs to be the same as the displayName and the adminConsentDescription needs to be the same as description. The id needs to be the same and isEnabled needs to be the same to.
If you don’t do this and the value is the same you will get an error when trying to save the manifest.
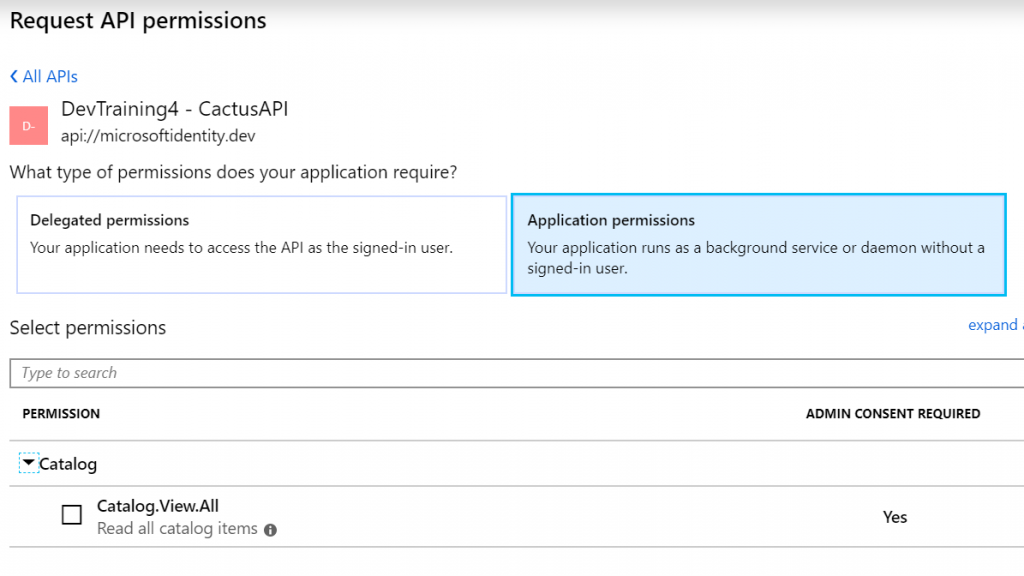
If I now go to my daemon app and request API permission they will show up in both types of permissions. First is the Application permissions screen:
Second is the Delegated permissions screen:
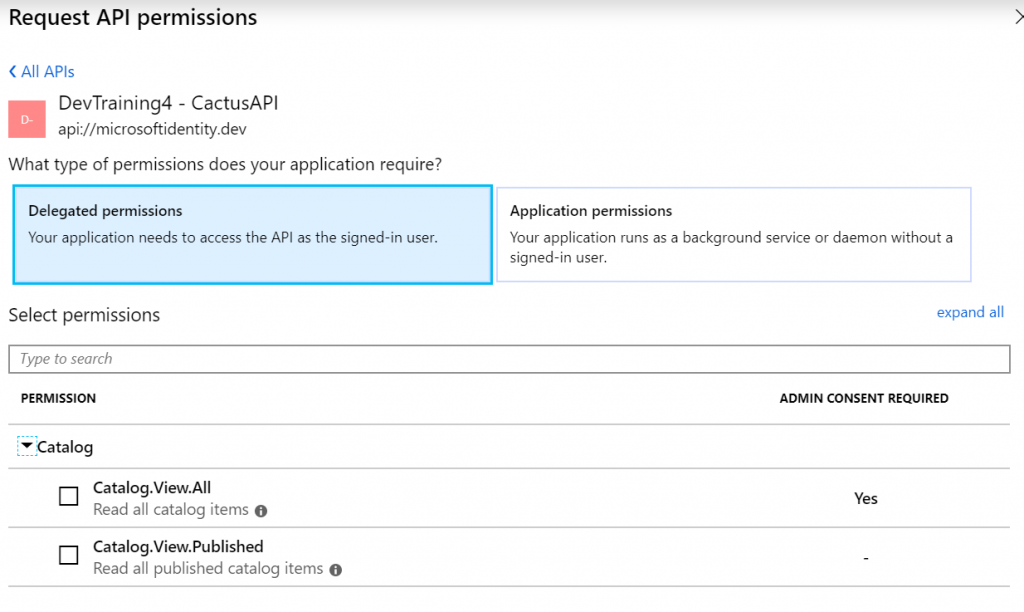
We really should have a UI to be able to this so you don’t have to do this by hand and make the mistakes I made to get this to work. The team is working on this, I just don’t know what the exact timeline is.
Let me know if this was useful for you and if you are using this to protect your own APIs with our identity platform.